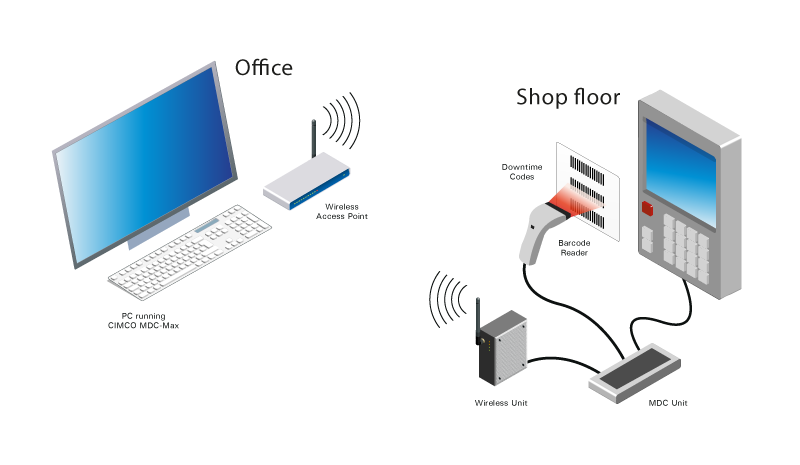
Barcode Downtime Data Collection Software
What is Automatic Identification and Data Capture (AIDC)? Automatic Identification and Data Capture (AIDC) is a broad category of technologies used to collect information from an individual, object, image or sound without manual data entry.
Inventory Management and Warehouse Operations Links. Below is my list of links to Inventory Management, Manufacturing, Material Handling, and Warehousing related sites. The Investor Relations website contains information about Trimble Inc. The Data Station Plus (DSP) was designed to act as a nexus for industrial data collection and management. 6273 Microsoft Windows Security Auditing Event. The unit offers multiple protocol conversion, data logging.
Sectors that use AIDC systems include distribution, manufacturing, transportation, medicine, government and retail, among many others. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. AIDC applications typically fall into one of a few categories: identification and validation at the source, tracking, and interfaces to other systems. The actual technologies involved, the information obtained and the purpose of collection vary widely. Current AIDC technologies include: Barcodes, which consist of small images of lines (bars) and spaces affixed to retail store items, ID cards and postal mail to identify a particular product number, person or location. A barcode reader uses a laser beam that is sensitive to the reflections from the line and space thickness and variation. The reader translates information from the image to digital data and sends it to a computer for storage or for another process.
D barcodes store information not only horizontally, as one- dimensional barcodes do, but vertically as well. That construction enables 2. D codes to store up to 7,0. The traditional, unidimensional barcode has a 2. Magnetic stripes, which are typically seen on credit cards, debit cards, key cards and swipe cards. The stripe consists of iron- based magnetic particles in plastic- like tape. Each particle is a tiny bar magnet.
Information is written on the stripe by magnetizing the tiny bars in either a north or south pole direction. The writing process, called flux reversal, causes changes in the magnetic field that can be detected by a magnetic stripe reader. Smart cards, which are plastic cards about the size of a credit card with an embedded microchip. A smart card can store much more data than a magnetic stripe card. It can be loaded with data, used for telephone calling, electronic cash payments, accessing services and other applications.
The card can be refreshed for reuse. Some smart cards can include programming and support multiple applications.
Optical character recognition (OCR), which is the recognition of printed or written textcharacters by a computer. The process includes scanning the text character- by- character, analyzing the resulting character image and translating that image into a machine- readable character code, such as ASCII. Among other things, OCR is used to digitize documents and books, sort mail, and process checks and mail- based payments by credit cards. Radio frequency identification (RFID) systems, which consist of three components: an antenna and transceiver (often combined into a single device) and a transponder (the tag).
EnterpriseIQ MES offers a complete manufacturing execution software solution to prevent costly downtime, while increasing manufacturing efficiency, quality and profit. Learn how data mining and business intelligence (BI) reporting will help you to evaluate decisions, find trends and answer questions. Find out how different.
The antenna transmits a signal that activates the transponder, which then transmits data back to the antenna. The data is used to notify a programmable logic controller that some specific action should occur. Because RFID does not require direct contact or line- of- sight scanning, RFID tags are replacing barcodes in many applications. Various biometrics applications, which identify individuals by comparing captured biological data, such as fingerprints, voice characteristics and iris patterns, against stored data for that individual. Authentication by biometric verification is becoming increasingly common in corporate and public security systems, consumer electronics and point of sale (POS) applications. Specific biometric AIDC technologies include fingerscanning, electro- optical fingerprint recognition, finger vein ID and voice recognition.

Providing Information for Best Value Awards! Welcome to the Past Performance Information Retrieval System (PPIRS). All data in PPIRS is classified as Source Selection.
Pen Computing and Rugged PC Review cover all aspects of mobile and rugged computing, including reviews of rugged and semi-rugged notebooks, Tablet PCs, slates. A smart barcode scanner app for fast barcode scanning with the device camera or accessory. Create barcode scanning workflows and sync data in the cloud. Check out the features of Maintenance Connection's CMMS/EAM software solution. Network Visibility & Analytics. Scale your network quickly, cut costs and monetize your data assets with Brocade’s comprehensive suite of software-based.
LS3. 40. 8- ER Corded Barcode Scanners from Symbol Technology. Extended range rugged scanner. Redefining performance for maximum industrial mobility.
The rugged Symbol LS3. ER handheld scanner from Motorola delivers superior performance and versatility for your scan- intensive industrial applications.
In the yard, warehouse, distribution center, manufacturing plant or retail store, the Symbol LS3. ER handheld scanner offers best- in- class performance, excellent reliability and user- friendly ergonomics to create a more productive mobile environment. Multiple on- board interfaces ensure flexible plug and play host connectivity.
Industry- leading impact tests ensure reliable performance in spite of the inevitable accidental drops. The device is impervious to dust and water, and its exit window is scratch- resistant and recessed for the highest level of durability. As a result, you avoid unnecessary equipment downtime or expensive equipment replacement costs. Two large LED- enhancing windows and an extra loud 8. When you choose the Symbol LS3.
ER, you receive the added assurance of purchasing from Motorola — a company with proven advanced data capture capabilities and millions of scanner installations worldwide. H x 4. 8. 2 in. W x 2. D 1. 8. 6. 5 cm H x 1. W x 7. 4. 3 cm D. Weight (without cable). Power Requirements.
Stand- by Current. Power Sources. Depending on host. External power supply. Twilight Black/Yellow. Performance Characteristics. Scanner Type. Retrocollective. Light Source. 6. 50 nm visible laser diode.
Scan Repetition. 3. Minimum Element Width. Working Distance. See Decode Zone. Print Contrast.
Roll (Tilt): 1. +/- 1. Skew (Yaw): 3. +/- 6. Decode Capability.
UPC. EAN, UPC. EAN with Supplementals, UCC. EAN 1. 28, JAN 8 & 1. Code 3. 9, Code 3. Full ASCII, Code 3. Trioptic, Code 1. Code 1. 28 Full ASCII, Codabar (NW7), Interleaved 2 of 5, Discrete 2 of 5, Code 9. MSI, Code 1. 1, Code 3.
Bookland EAN, IATA, UCC/EAN RSS and RSS variants. Interfaces Supported. RS2. 32, Keyboard Wedge, Wand Emulation, Scanner Emulation, IBM 4. X/4. 69. X, USB and Synapse. User Environment.
Operating Temperature. See full warranty for details.