Create Certificate Request Apache Windows Client
How to setup OpenSSL to create certificates. 5) Create a root certificate. All other certificates you create will be based off of this.
Apache CXF - - Client HTTP Transport (including SSL support)Authentication. Basic Authentication < conduit name=. The full. Header is the Authorization Header the server sent after the last try. This way you can implement multi phase authentications. You are expected to return the authorization Header to send to the server.
For a simple implementation you can look at org. Default. Basic. Auth. Supplier. If you set your implementation class as Auth. Supplier on the conduit CXF will use it. Spnego Authentication (Kerberos)Starting with CXF 2. CXF supports Spnego authentication using the standard Auth. Policy mechanism.
Spnego is activated by setting the Auth. Policy. authorization. Type to 'Negotiate'. If user. Name is left blank then single sign on is used with the TGT from e.
Windows Login. If user. Name is set then a new Login. Context is established and the ticket is created out of this. By default the Spnego. Auth. Supplier uses the OID for Spnego.
Some servers require the OID for Kerberos. This can be activated by setting the contextual property auth. Kerberos. Oid to 'true'. Kerberos Config: Make sure that krb.
Kerberos realm you want to authenticate against and supply it to your application by setting the java. Login Config: Create a file login. CXF using the System property java.
Generating your Apache CSR with OpenSSL. Easy instructions to create your CSR (certificate signing request) for Apache web servers using OpenSSL. Hi Jonas, The OID (object identifier) identifies the permitted certificate key usage. For example a certificate than can be used for server authentication includes an. Learn how to create an Apache self signed certificate to secure your Apache web server with SSL for free. Apache Axis Client Tips and Tricks. As I was developing Stubby (a Lotus Notes database that helps you create Apache Axis "stub" files that can be used to call web. Apache Kafka on Heroku is a fully managed and integrated Kafka offering on the Heroku platform.
SSL (Secure Socket Layer) is used for encryption and decryption, processing of S/MIME signed or encrypted mails, generation of certificates and more. To use it on. Professional web developers need a web server and Apache is the most popular. It is pre-installed in Linux and Mac OS, but what about Windows? Craig provides a step. How to use client certificates with apache. This How-To is intended to give a step-by-step configuration guide for creating your own certificate authority (CA) and.
The file should contain: CXFClient . If you want to use the cached Ticket Granting Ticket then do not supply them.
On windows you will also have to make sure you allow the TGT to be used in Java. See: http: //www.
Note that setting this property will let the receiving service implement the credential delegation. If the Kerberos credential is already available in the service request context then one can make this credential available to Spnego/Kerberos authentication handler by setting it on the current CXF message, using an 'org. GSSCredential' key. This can be done before a client invocation is made, by setting a client request context property, or by extending 'org.
Abstract. Spnego. Auth. Supplier'. Please see this thread for more information on the latter option. Note in the case of reusing the existing credential, the policy configuration does not need to reference a login module name: .. On Java 6, NTLM authentication is built into the Java runtime and you don't need to do anything special. On Java 5, you need a library that will augment the Http. URLConnection to do it. See: http: //jcifs.
Note: jcifs is LGPL licensed, not Apache licensed. Next, you need to configure jcifs to use the correct domains, wins servers, etc..
Notice that the bit which sets the username/password to use for NTLM is commented out. If credentials are missing jcifs will use the underlying NT credentials.//Set the jcifs properties. Config. set. Property(. The reason is that the NTLM authentication requires a 3 part handshake which breaks the streaming.//Turn off chunking so that NTLM can occur.
Client client = Client. Proxy. get. Client(port). HTTPConduit http = (HTTPConduit) client. Conduit(). HTTPClient. Install Amx Mod X Manually Install there.
Policy http. Client. Policy = new HTTPClient. Policy(). http. Client. Policy. set. Connection. Timeout(3. 60. 00). Client. Policy. set. Allow. Chunking(false). Download Mods For Farming Simulator 2013 Map there.
Client(http. Client. Policy). Please also see Asynchronous HTTP Conduit for more information on NTLM. Configuring SSL Support.
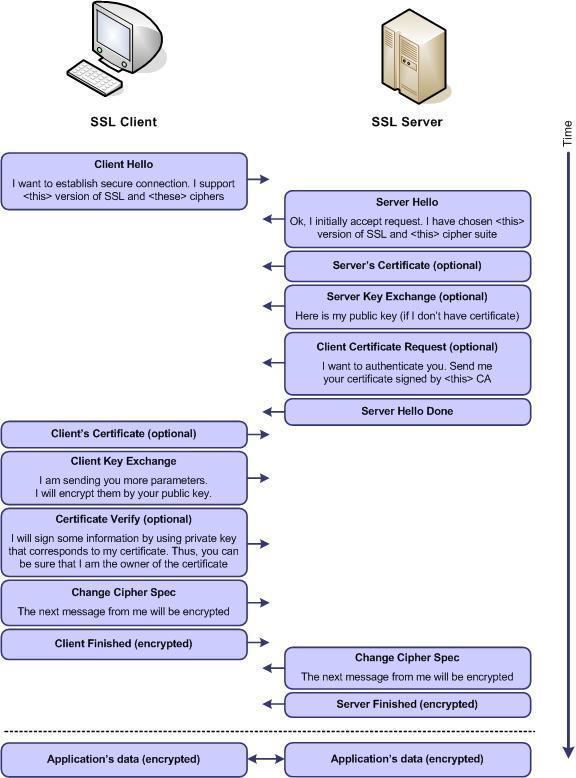
When using an . For many HTTPs applications, that is enough and no configuration is necessary. However, when using custom client certificates or self signed server certificates or similar, you may need to specifically configure in the keystores and trust managers and such to establish the SSL connection. To configure your client to use SSL, you'll need to add an < http: conduit> definition to your XML configuration file.
See the Configuration guide to learn how to supply your own XML configuration file to CXF. If you are already using Spring, this can be added to your existing beans definitions.
A wsdl. Also see this blog entry for another example. Here is a sample of what your conduit definition might look like: < beans xmlns=. This allows CXF to associate this HTTP Conduit configuration with a particular WSDL Port. The name includes the service's namespace, the WSDL port name (as found in the wsdl: service section of the WSDL), and . It follows this template: . Note: it's the PORT name, not the service name. Thus, it's likely something like .
If you are having trouble getting the template to work, another (temporary) option for the name value is simply . The configuration is matched at conduit creation so the address used in the WSDL or used for the JAX- WS Service.
For example, you can do: < http: conduit name=. If you have multiple clients interacting with different services on the same server, this is probably the easiest way to configure it. If your service endpoint uses an SSL WSDL location (i. The specific HTTP conduit name or a reg- ex expression can still be used. Keystores (as identified by the sec: key. Store element above) can be identified via any one of three ways: via a file, resource, or url attribute. File locations are either an absolute path or relative to the working directory, the resource attribute is relative to the classpath, and URLs must be a valid URL such as .
Only one attribute of . It is commonly referred to using the prefix http- conf. In order to use the HTTP configuration elements you will need to add the lines shown below to the beans element of your endpoint's configuration file. In addition, you will need to add the configuration elements' namespace to the xsi: schema. Location attribute.< beans .. The http- conf: conduit element takes a single attribute, name, that specifies the WSDL port element that corresponds to the endpoint. The value for the name attribute takes the form port.
QName. http- conduit. For example, the code below shows the http- conf: conduit element that would be used to add configuration for an endpoint that was specified by the WSDL fragment < port binding=. Alternatively, the name attribute can be a regular expression to match a URL. This allows configuration of conduits that are not used for purposes of WSDL based endpoints such as JAX- RS and for WSDL retrieval..
They are described below. See also Sun's JSSE Guide for more information on configuring SSL. Element. Descriptionhttp- conf: client. Specifies the HTTP connection properties such as timeouts, keep- alive requests, content types, etc. Specifies the the parameters for configuring the basic authentication method that the endpoint uses preemptively. Authorization. Specifies the parameters for configuring basic authentication against outgoing HTTP proxy servers.
Client. Parameters. Specifies the parameters used to configure SSL/TLS. Supplier. Specifies the bean reference or class name of the object that supplies the authentication information used by the endpoint both preemptively or in response to a 4. HTTP challenge. http- conf: trust.
Decider. Specifies the bean reference or class name of the object that checks the HTTP(S) URLConnection object in order to establish trust for a connection with an HTTPS service provider before any information is transmitted. The client element. The http- conf: client element is used to configure the non- security properties of a client's HTTP connection. Its attributes, described below, specify the connection's properties.
Attribute. Description. Connection. Timeout. Specifies the amount of time, in milliseconds, that the client will attempt to establish a connection before it times out. The default is 3. The default is 6. The default is false. Max. Retransmits.
Specifies the maximum number of times a client will retransmit a request to satisfy a redirect. The default is - 1 which specifies that unlimited retransmissions are allowed. Allow. Chunking. Specifies whether the client will send requests using chunking. The default is true which specifies that the client will use chunking when sending requests. By default, messages less than 4.
K are buffered and sent non- chunked. Once this threshold is reached, the message is chunked.
