Where Do You Download Apps For Jailbroken Ipad Apps
Ways to Install Apps On an i. Pad. First, you should check to see if the app is updated in the App Store. If your app is up to date, try turning off your i. Pad and then restarting it. Finally, you can delete and re- download the app. Install Rgl Package R Windows Command more. There's a possibility the app is broken, too- -often times, when an app stops running, it's because of a developer issue or a software update, so you should definitely wait for an appropriate app update to fix it.
We also discuss what measures you should implement to ensure your device is safe, and we evaluate whether the i. Phone and i. Pad are safe from malware. According to Apple the i.
You've got yourself an Apple tablet, and you're bewildered by the sheer volume of apps. Just download these, and your life will be better. How to Install Apps On an iPad. The iPad has a wide array of apps available for download from the App Store, with is a default program on all iOS products. Do Android phones finally have better apps than the iPhone? The iTunes App Store has historically been the first choice for developers, but things are changing.
OS platform is completely secure. The company even states that it . Keeping information secure on mobile devices is critical for any user, whether they’re accessing corporate and customer information or storing personal photos, banking information, and addresses. Because every user’s information is important, i. OS devices are built to maintain a high level of security without compromising the user experience.
However, Apple's i. OS platform for the i. Pad and i. Phone hasn't been without its security breaches and vulnerabilitiies, and nor has i.
Cloud, the cloud storage service which makes it possible to access documents, photos and more on all of your Apple devices. Read on to find out about: The latest security exploits to affect i.
OS on the i. Phone and i. Pad: What you need to know about Xcode. Ghost. In the lastest security exploit, which was identified around 2. September, some developers - located in China - have used the incorrect program to create apps for the i. OS app store. It is thought that the developers downloaded a fake version of Xcode because it was taking too long to download Xcode from Apple’s own servers, which are hosted in the US. Xcode weighs in at around 3.
Download or update iTunes to the latest version. On the device, head to Settings > iCloud and disable Find my iPhone/iPad if it’s on. Connect your iOS device to.
GB in total. The Chinese developers were using Xcode. Ghost rather than Apple’s Xcode.
While the affected apps are Chinese, there are a few popular apps among them such as Angry Birds 2, although Rovio has confirmed that only the Chinese App store version of Angry Birds 2 is vulnerable, and that a fix is coming soon, according to 9to. Mac. Apparently 3. Palo Alto Networks, there is a full list on 9to. Mac. However, there may in fact be more than 3. Chinese security firm who said it found 3. V3. It seems that only apps purchased from the Chinese App Store are affected though.
Apple began addressing the issue on Sunday after being alerted to the fact that Xcode. Ghost had been embedded in some apps.
This is the first major breach of the App Store, before this exploit their had only been five instances of affected apps. Android’s open ecosystem, on the other hand, leaves the door open to security issues. Each app goes through a careful review process before Apple allows it into the store. Unfortunately, this time the Xcode malware made its way past Apple’s reviews. What other security exploits have affected i. OS on the i. Phone and i. Pad. 20. 14 was a year of security vulnerabilities and targetting of i.
OS. First off, a security flaw was discovered in late February 2. Starbucks or an internet caf. Apple claims that the privacy breach was not the result of a compromise of any of the systems used for its i. Cloud storage service.
However, through some means hackers were able to access celebrity photos that were stored in i. Cloud. Then in November the first malware with the potential to infect all i. Phones and i. Pads was discovered by security firm Palo Alto Networks. Malware affecting jailbroken devices is nothing new but Wire. Lurker - as the researchers christened it - used a two- stage attack involving USB connections via a Mac or PC, and a glitch in an i. OS feature that allows organisations to install their own apps on non- jailbroken i. OS devices. While Wire.
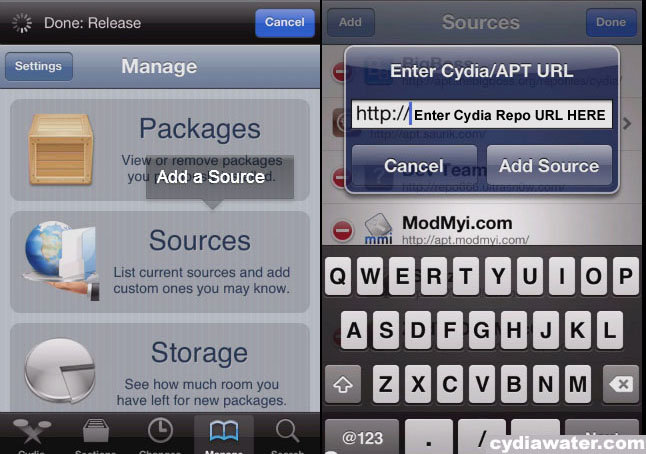
- Free Jailbreak iOS 6.0 - 9.3.5 & 10.0.2 - download for your iPhone, iPad or iPod touch. Easy, Free, Safe and Fast. Jailbreakme, pangu, taig, redsnow, Cydia.
- If you'd like a.
- Are you ready for the iOS jailbreak? Get the iOS Jailbreak here. The best cydia apps and cydia tweaks on the web, Download Cydia, and get Cydia for your iOS device.
- With our online tool you will easily jailbreak or unlock iPhone, iPad, iPod.
Lurker installed malicious apps on jailbroken phones and plundered them of personal information - including the device’s phone number and i. Cloud address book - non- jailbroken phones got off more lightly, with just a benign pirated comic book app invisibly installed on the phone. Basic diagnostic data was also passed to a central command server. Apple has since blocked Wire. Lurker on both i. OS devices and Macs but experts suggest that the technique used will give rise to further attacks. Sure enough, just a week after Wire.
Lurker stole the headlines, another i. OS 8 malware threat emerged.
This threat, known as Masque Attack creates decoy apps that are like those on your i. Phone, and these decoy apps attempt to steal your personal information.
According to Fire. Eye, who spotted the threat, Masque Attacks can pose much bigger threats than Wire. Lurker. So, following these recent situations, can Apple maintain its stance that i. OS is secure. We examine the various cases that have begged the question of security on the i.
OS platform, we look at how to make sure your i. Phone or i. Pad is secure (and the problems some people have experienced when updating their device), and we asking whether this mean that Apple's i. OS isn't secure? Read on to find out.. PART 1: Security threats to i. OS devices. We examine the Xcode.
Ghost, Wire. Lurker and Masque Atteck malware, the Olag Pliss ransom case and the SSL flaw. Plus: What really happened in the Jennifer Lawrence nude images leak?
Is Xcode. Ghost a threat? Palo Alto Networks, however the affected apps are developed in and hosted in China, so it is unlikely that you will be running any of them on your i. Phone or i. Pad, unless you had downloaded them from the Chinese App Store.
For example, while Angry Birds 2 is affected by the exploit, apparently it is only the Chinese App Store version that is affected. If you are in China, Apple has already removed the affected apps from the App Store. Was Masque Attack a threat? Masque Attack, a threat spotted by Fire.
Eye, creates decoy apps that mimic those on your i. Phone and steal your personal information. Apple was able to block Wire. Lurker by blocking enterprise certificate that it was using to install malicious apps, but Masque Attack uses the same bundle identifiers as existing apps instead. According to Fire.
Eye: “This vulnerability exists because i. OS doesn't enforce matching certificates for apps with the same bundle identifier.”To avoid being compromised by Masque Attack, only install apps that come directly from the App Store, don’t click on Install if you see a pop- up on a website or if you see a prompt to install an update to an app like Flappy Bird. Also, if i. OS displays an alert that an app is from an Untrusted App Developer tap Don’t Trust and uninstall it. At its worse the malware could replace Gmail or banking apps with a fake apps that would steal your data you give it.
Fire. Eye said: “We verified this vulnerability on i. OS 7. 1. 1, 7. 1. An attacker can leverage this vulnerability both through wireless networks and USB.”Apple has released a statement to i. More, claiming that Masque Attack isn’t really a flaw and that it is unaware of anybody who has been affected.
Because the attack relies on someone actually responding to a dodgy link and downloading an app from somewhere other than the App Store, having ignored a warning about downloading malicious apps, Apple is confident that it has adequate barriers in place to stop people being affected by this particular malware. However, the best barrier would be to make it impossible to install an app from somewhere other than the App Store, or a company’s own servers or secure- website if it is an in- house app.
Was Wire. Lurker a threat? How To Install Mods Gta San Andreas Android Games. Wire. Lurker was a Trojan that was inserted into pirated Mac OS X software, such as popular game titles, as well as within simple Windows executables that promised to install pirated apps on a user’s i. OS device. Notably, although Wire. Lurker infected i. OS devices, it wasn’t malware in the traditional sense in that one i.
OS device did not spread the infection to another. Wire. Lurker could only delivered via a USB connection to a Mac or Windows computer following the download of dodgy software offered on various Chinese websites. The infected software was downloaded over 4. Wire. Lurker possibly the biggest outbreak of i. OS malware yet detected. Windows users got off lightly because the version of Wire.
Lurker used was older and so buggy that it was essentially useless. It also targeted only jailbroken devices. The version of Wire. Lurker infecting Macs was significantly more sophisticated.